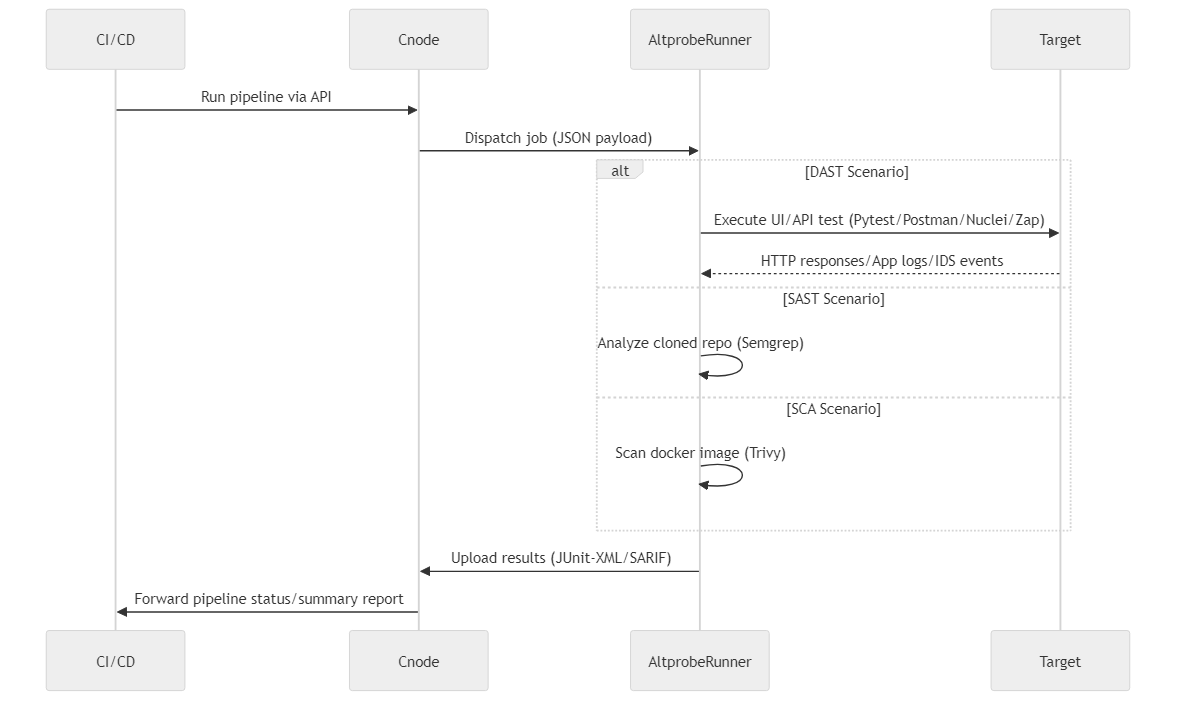
Architecture#
Alertflex project combines automated testing, DAST scanning, and infrastructure monitoring within DevSecOps, accelerating development and improving software quality.
High-level design#
The solution is designed for hybrid IT infrastructures, supporting both on-premises and cloud-based deployments. It functions as a Tests/DevSecOps orchestrator with integration support for 10+ different tools (primarily open-source).
Alertflex consists of two main system components:
altprobe: The collector/runner agent.
cnode: The controller and management console.
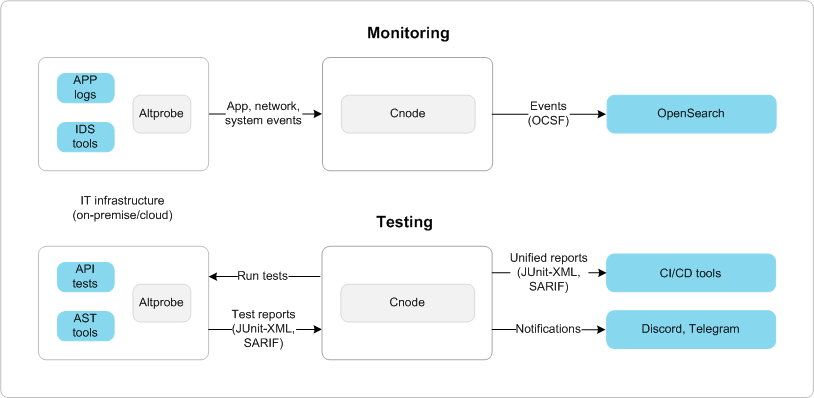
As shown in the diagram, Alertflex can operate in two modes: monitoring and testing.
Note: Testing mode is not currently available for installations from GitHub.
Operation Modes#
Monitoring Mode#
The collector reads events from application logs, Falco, and Suricata. It can ingest data directly from log files or from a Redis list using the RPOP command. The collector then converts these events into the Open Cybersecurity Schema Framework (OCSF) format and sends them to the cnode. The cnode, in turn, streams the events into OpenSearch and its Security Analytics plugin. Additionally, OCSF dashboards can be used for event visualization to make threat detection and analysis easier.
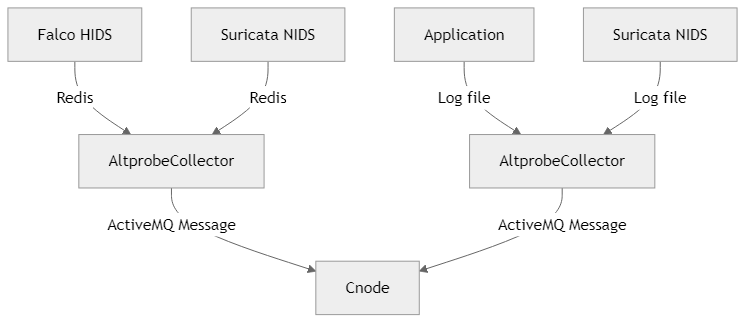
Supported Log Format
Application logs should follow this structure:
Timestamp: ISO 8601 format
Level (e.g., INFO, WARN, ERROR)
Logger name: Optional, enclosed in brackets (e.g.,
[security])File name and line number of the caller
Message
Structured data: Optional JSON-encoded data
Example
2025-01-10T18:24:10.1430-0200 INFO log/core_test unnamed global logger
Testing Mode (Distributed Test Execution - Not currently available)#
In this mode, the runner component:
Performs active scanning and vulnerability checks.
Executes configured test suites.